
ProLock ransomware emerged on the threat scene in March, a retooled and rebranded version of PwndLocker.
As SophosLabs reveals in its detailed analysis, while ProLock ransomware gives you the first eight kilobytes of decryption for free, it can still cause significant business disruption and economic damage.
Intercept X gives you multiple layers of protection against ProLock, keeping the data on your endpoints and servers safe:
If you’re running Sophos Intercept X you can relax knowing that you are automatically protected against ProLock, as all three of the above features are enabled by default in our recommended settings.
(If you’re not yet running Intercept X and want to give it a try, visit the web page to learn more and start a no-obligation free trial.)
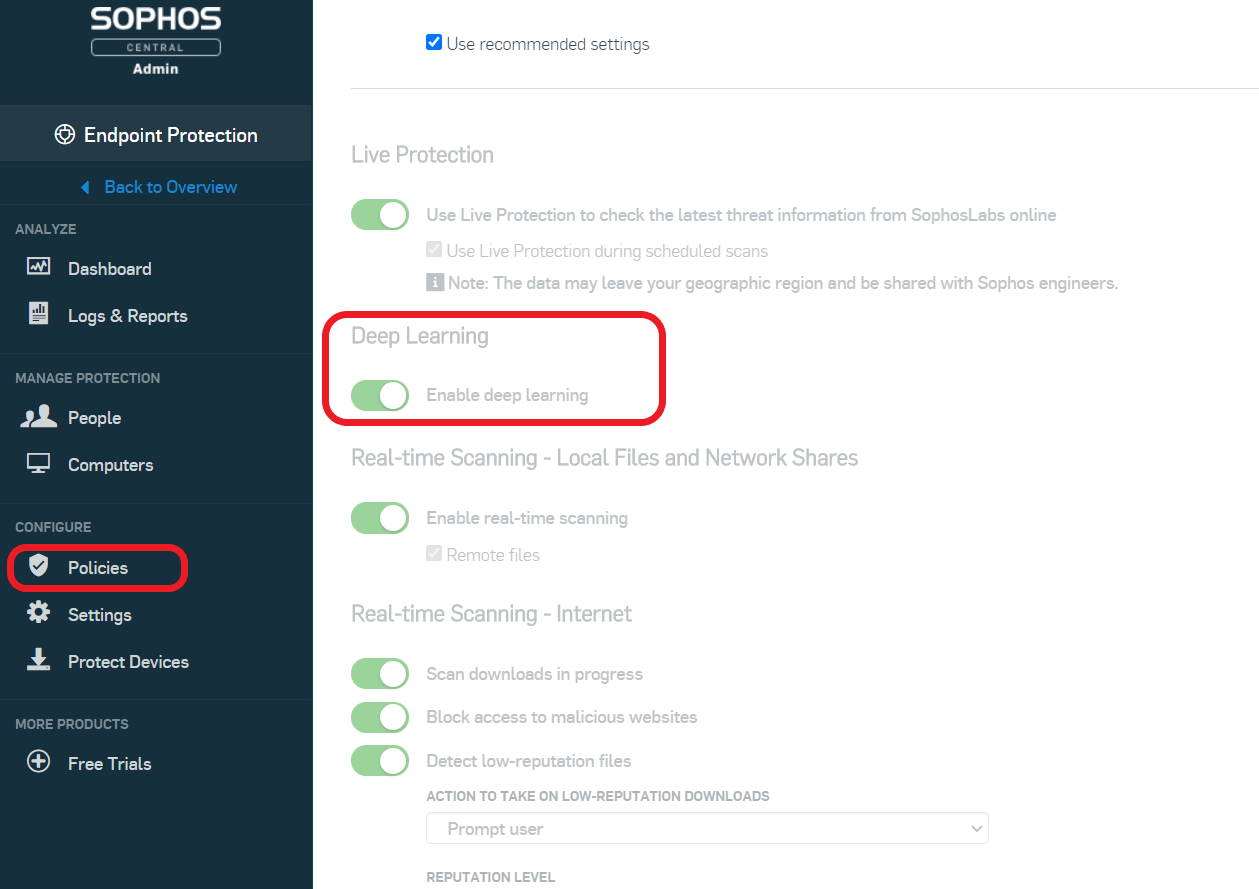
To check that you have CryptoGuard and Deep Learning enabled:
51% of IT managers surveyed for our recent State of Ransomware 2020 report said their organization was hit by ransomware last year, and that cybercriminals succeeded in encrypting data in 73% of incidents.
With stats like these it’s worth taking the time to ensure all your ransomware defenses are up-to-date.
The earliest detection of ProLock by Sophos was traced to a compromised server, most likely through an exploit of a Remote Desktop Protocol (RDP).
Putting RDP access behind a virtual private network and using multi-factor authentication for remote access are just a couple of the best practices we recommend to reduce your ransomware risk.
For additional best practices, take a look at our guides Endpoint Protection Best Practices to Block Ransomware and Firewall Best Practices to Block Ransomware.
4909 Murphy Canyon Road Suite, 500
San Diego, CA 92123
Store
Company
Support
Newsletter
Technology Solutions You Can Trust Dismiss