
PrintNightmare is a zero-day critical Windows bug that allows Remote Code Execution. It affects all supported Windows machines, including both endpoints and servers. For more information on the bug, please read the article on Naked Security.
As of 1 July 2021, there is no official patch yet to address this bug. Given the severity, we anticipate that Microsoft will release a fix as soon as possible.
SophosLabs is working on generating protection for PrintNightmare as a priority.
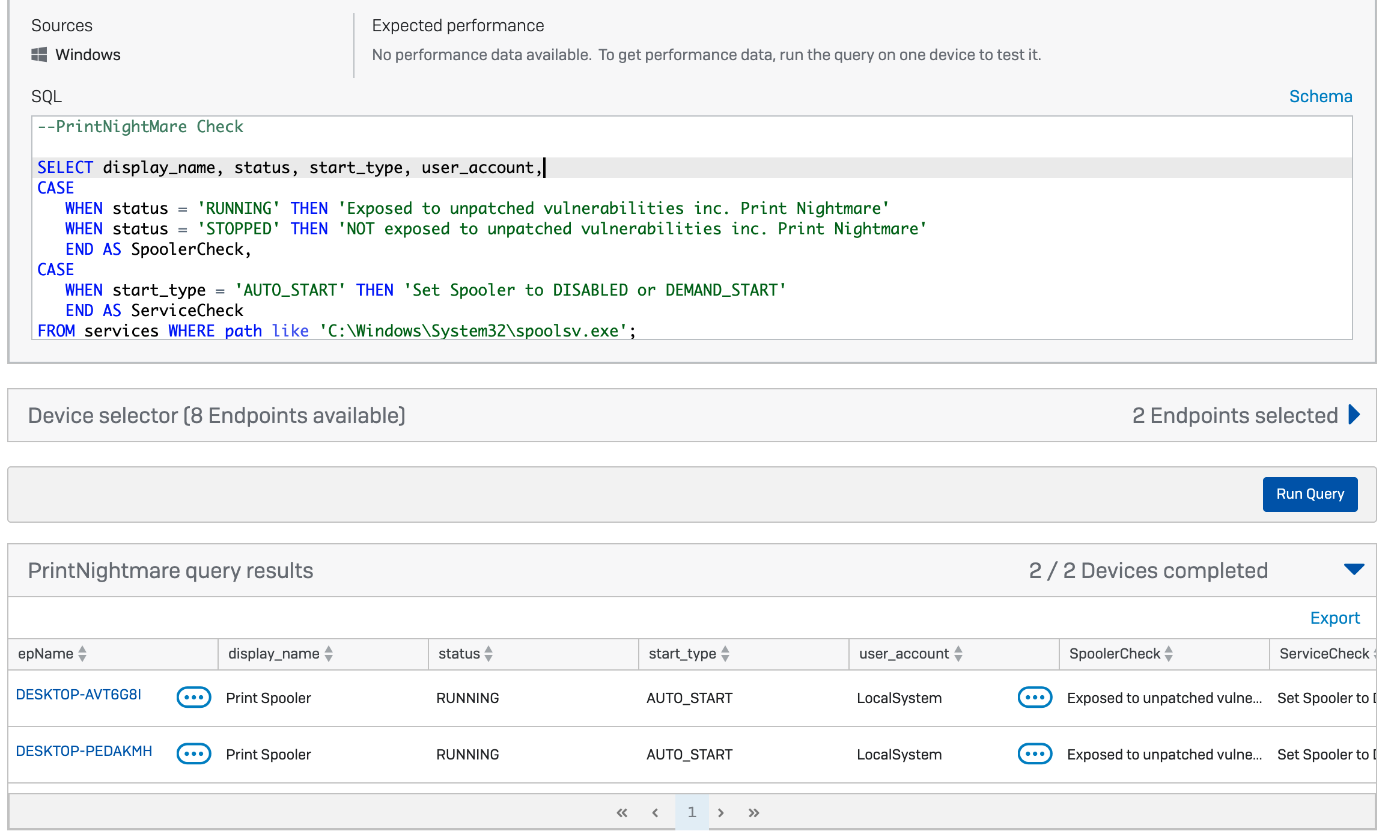
SELECT display_name, status, start_type, user_account, CASE WHEN status = 'RUNNING' THEN ' Exposed to unpatched vulnerabilities inc. PrintNightmare' WHEN status ='STOPPED' THEN ' NOT exposed to unpatched vulnerabilities inc. PrintNightmare' END AS SpoolerCheck, CASE WHEN start_type = 'AUTO_START' THEN 'Set Spooler to DISABLED or DEMAND_START' END AS ServiceCheck FROM services WHERE path = 'C:WindowsSystem32spoolsv.exe';
Your query should look like this:
Organizations using Sophos protection managed through Sophos Central can activate Sophos EDR for free, for 30 days using the Free Trials feature within their Sophos Central console.
To see if the Spooler service is running on your computer, you can use the Windows SC (Service Control) command from a command prompt Window, e.g.
C:Usersduck>sc query spooler
SERVICE_NAME: spooler
TYPE : 110 WIN32_OWN_PROCESS (interactive)
STATE : 4 RUNNING
(STOPPABLE, NOT_PAUSABLE, IGNORES_SHUTDOWN)
WIN32_EXIT_CODE : 0 (0x0)
SERVICE_EXIT_CODE : 0 (0x0)
CHECKPOINT : 0x0
WAIT_HINT : 0x0
You can prevent the spooler starting by itself, even after a reboot, with:
C:Usersduck>sc config spooler start= disabled
Note that there must be no space between the word start and the = character, but you do need a space between the = sign and the word disabled. You need to start your command prompt (CMD.EXE) as Administrator to reconfigure services.
Reboot and you should see this:
C:Usersduck>>sc query spooler
SERVICE_NAME: spooler
TYPE : 110 WIN32_OWN_PROCESS (interactive)
STATE : 1 STOPPED
WIN32_EXIT_CODE : 1077 (0x435)
SERVICE_EXIT_CODE : 0 (0x0)
CHECKPOINT : 0x0
WAIT_HINT : 0x0
We will update this article with further information once available.
4909 Murphy Canyon Road Suite, 500
San Diego, CA 92123
Store
Company
Support
Newsletter
Technology Solutions You Can Trust Dismiss