
App developers have, for years, embedded ad-code into their apps as a way to help defray the costs of development, but some developers simply use their apps as a borderline-abusive platform solely to launch ads on mobile devices.
SophosLabs recently discovered 15 apps on Google’s Play Market that engage in such practices; They generate frequent, large, intrusive ads and literally hide their app icons in the launcher in order to make it difficult for you to find and remove them. Several of them go a step further by disguising themselves in the phone’s App settings page.
According to the Play Market pages for these apps, more than 1.3 million devices worldwide have installed at least one of them. If history is any indication, there are likely many more waiting to be found.
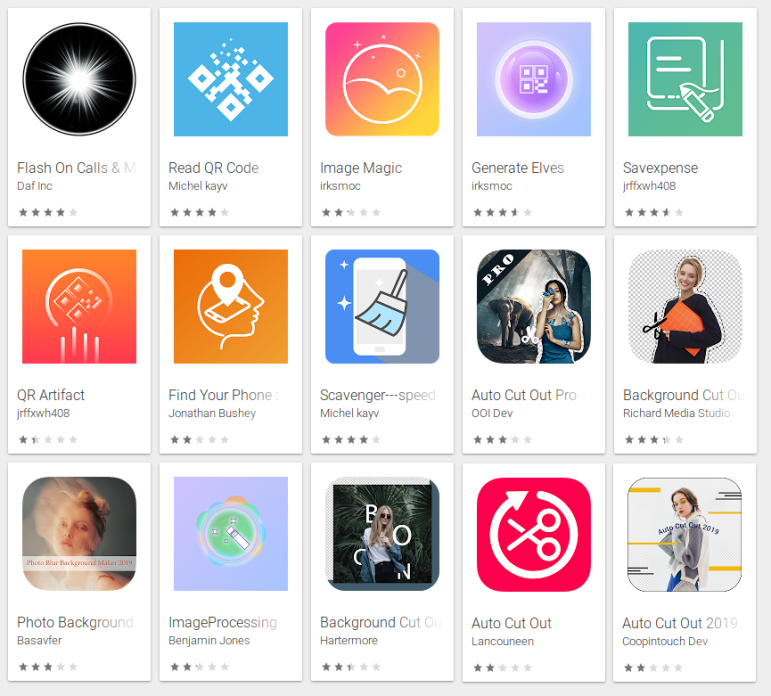
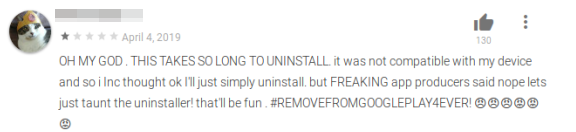
For example, the app free.calls.messages (Flash On Calls & Messages – aka Free Calls & Messages – shown below) engages in some clever trickery to prevent users from uninstalling the app.
When first launched, the app displays a message that says “This app is incompatible with your device!” You might think that the app has crashed, because, after this “crash,” the app opens the Play Store and navigates to the page for Google Maps, to mislead you into thinking that the ubiquitous Maps app is the cause of the problem. It is not. This is a ruse.
The app then hides its own icon so it doesn’t show up in the launcher’s app tray. Others in the list hide their icon, too: Some do this on the first launch, while others simply wait for a while after you install the app.
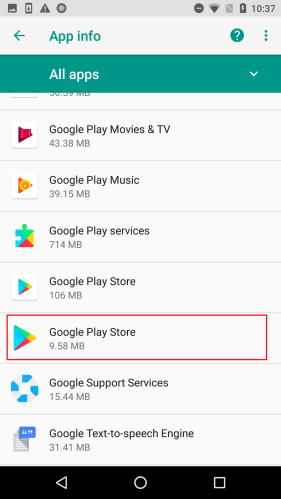
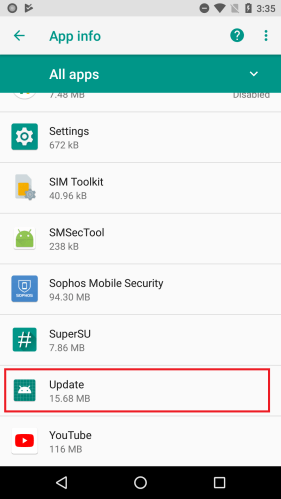
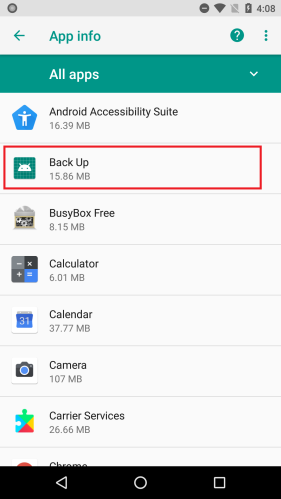
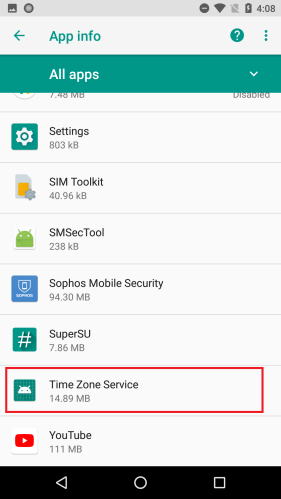
SophosLabs has also observed these apps pulling a different dirty trick: using one name and icon for the application (which is visible in the phone’s Apps settings page), and a different name and icon for the Main Activity (the running app window).
Nine out of the batch of 15 apps used deceptive application icons and names, most of which appeared to have been chosen because they might plausibly resemble an innocuous system app. (The app icon is still visible in the phone’s “gear” Settings menu, under Apps.)
By hiding their launcher icon, and using an application icon and name that resembles a system app, these apps make a convincing case to a casual observer that there’s nothing unusual installed on the phone.

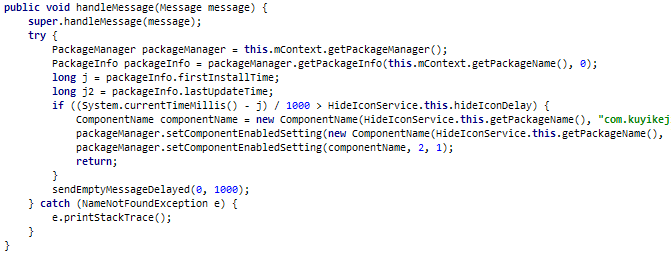
Other apps make use of a library, called koolib, that installs a service to hide the icon after a predetermined time after the installation of the app. Not kool, app.
Most of these apps were presented to the user as one kind of utility app or another. QR code readers, image editors, backup utilities, a phone finder, and most ironically. a utility ostensibly to . The apps further disguised themselves using a name representing a harmless app, such as Google Play Store, Update, Back Up, or Time Zone Service. These names appear only in the phone’s settings.
 |
 |
 |
 |
All of these apps appeared during this calendar year. The oldest one among these, free.calls.messages, was published in January; Two months after it appeared, it had more than a million installs. Although these apps were uploaded to the market by different publisher accounts, many shared similar code structure, UI, package names, and behavior — too many for it to be considered a coincidence.
For example, the app com.cc.image.editor contained a reference to a different app, com.bb.image.editor, within its code. The two apps, despite their similar names, were published by completely different entities. This suggests to us that the former might have been derived from the latter, but we can’t definitively say that the same author(s) developed both apps.
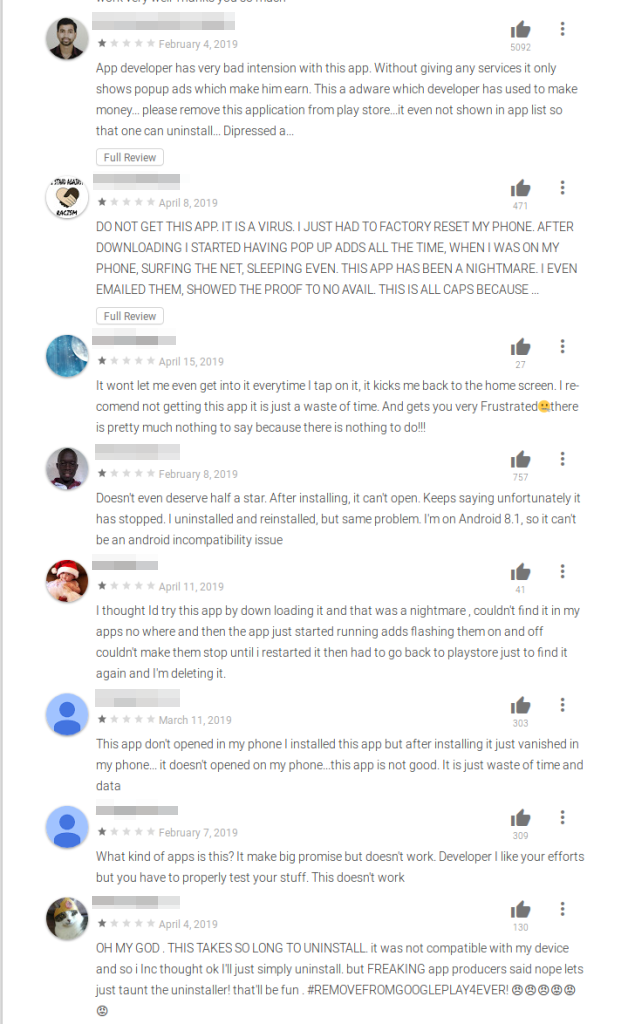
Most of these apps had negative reviews from users, many of which had complained about these apps not being able to run, app icon disappearing from the launcher, and of course the aggressive ads.
SophosLabs notified Google about these apps in July and, as far as we know, they have been taken down. These apps are detected by Sophos Mobile Security as Andr/Hiddad-AB and Andr/Hiddad-AC.
| Package Name | Installs | Published |
| free.calls.messages | 1,000,000+ | Jan 2019 |
| com.a.bluescanner | 10,000+ | May 2019 |
| com.bb.image.editor | 10,000+ | May 2019 |
| com.cc.image.editor | 100,000+ | June 2019 |
| com.d.bluemagentascanner | 10,000+ | June 2019 |
| com.doo.keeping | 1,000+ | May 2019 |
| com.e.orangeredscanner | 10,000+ | July 2019 |
| com.hz.audio | 10,000+ | June 2019 |
| cos.mos.comprehensive | 10,000+ | April 2019 |
| com.garbege.background.cutout | 10,000+ | July 2019 |
| com.hanroom.cutbackground | 50,000+ | July 2019 |
| com.jiajia.autocut.photo | 100,000+ | July 2019 |
| com.jiakebull.picture.background | 50,000+ | July 2019 |
| com.fruit.autocut.photo | 10,000+ | July 2019 |
| com.huankuai.autocut.picture | 10,000+ | July 2019 |
4909 Murphy Canyon Road Suite, 500
San Diego, CA 92123
Store
Company
Support
Newsletter
Technology Solutions You Can Trust Dismiss